Explore: Actor
The Actor Explore page provides analyst-curated information about Threat Actors. Our actor database focuses on state-sponsored actors, actors focusing on cybercrime, ransomware groups, access brokers, exploit brokers and buyers, or critical infrastructure attackers. The actor information will continue to grow as we add more content and hear from our customers. If you know of a new threat actor that should be included – please let us know!
To get started, navigate to the Explore section, and select Actor from the top menu. This will bring you to a landing page of Actor baseball cards.
- Use the < > icons to page through the list.
- Use the left options to filter and sort the actor list.
- Click on a baseball card, or search for an actor using the lookup bar at the top, to go to the actor’s detail page. You can look up actors by name, alias, CVE, or industry.

Once you select an actor, you will go to that actor’s detail page, opened to the Dossier.
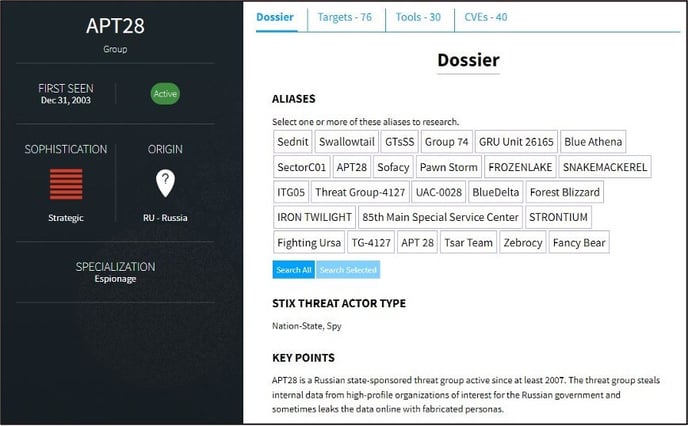
An actor entry may include the following tabs: Dossier, Darknet Fingerprint, Targets, Tools, or CVEs. Click on the name of he tab to navigate to that section; continue reading for more detail about the information contained within each tab.
Information within the Dossier page may include any of the following:
|
Aliases |
All Aliases by which the Actor is known. Click on an Alias to search within Vision for matches. |
|
Origin |
The country in which the Actor operates, if known. |
|
First Seen |
The date the Actor was first known to be active. |
|
Last Seen |
The date the Actor was last known to be active. |
|
Sophistication |
The level of sophistication at which the Actor operates, using STIX Threat Actor Sophistication Vocabulary: none, minimal, intermediate, advanced, expert, innovator, strategic. |
|
Specialization |
A categorization of the type of activity or area in which the Actor is known to participate. These values may include: Cyber Crime, Data Exfiltration, Espionage, Exploit Developer, Exploit Seller, Financial Crime, Hacker, Hacktivist, ICS Attacks, Initial Access Broker, Intellectual Theft, Phishing, Ransomware, Social Engineering. |
|
Size |
Identification of whether the Actor is an individual entity, a group, or unknown size. |
|
Key Points |
A brief narrative description. This section may also include may any known Law Enforcement Activity, if applicable. |
|
Stix Threat Actor Type |
A categorization of the type of Actor, using STIX Threat Actor Type vocabulary: activist, competitor, crime-syndicate, criminal, hacker, insider-accidental, insider-disgruntled, nation-state, sensationalist, spy, terrorist. |
|
Contact Details |
Email addresses that have been associated with the Actor. Tox IDs that have been associated with the Actor. Tox is a peer-to-peer instant messaging platform. Jabber addresses that have been associated with the Actor. Jabber uses the XMPP protocol. Telegram accounts that have been associated with the Actor. Discord accounts that have been associated with the Actor. |
|
Cryptocurrency |
Bitcoin, Ethereum, or Monero wallets that have been associated with the Actor. |
Information within the Darknet Footprint tab may include any of the following:
|
Operations |
Places on the darknet or messaging platforms that are known to be run by the actor. Click on the Search button to begin researching within a channel or domain. Channels: Telegram or Discord channels the Actor is known to operate or admininster. Domains: Darknet or other websites the Actor is known to operate or administer. |
|
Data Leaks |
Data leaks or breaches within the DarkOwl Vision dataset the Actor is known to have leaked. Click on the Search button to begin researching within a data leak. |
|
Presence |
A list of Forums and/or Markets on which the Actor has been observed. |
Information within the Targets, Tools, and CVEs pages includes:
|
Targets |
Industries and Organizations (or type of organizations) the Actor is known to have previously attacked. Clicking on a target will show other Actors in our database that have targeted the same industry or organization. |
|
Tools |
A list of known software Tools the Actor has used to carry out attacks. Clicking on a tool will show other Actors in our database that have used the same tool, and have an option to Compare them. The Compare functionality will show the timelines of each actor, as well as collisions in profile data. |
|
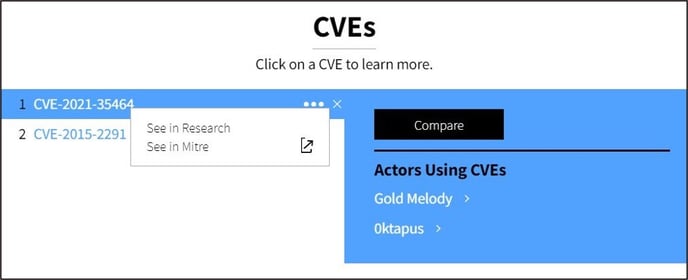
CVEs |
A list of known CVEs (Common Vulnerabilities and Exposures) the Actor has used to carry out attacks. Clicking on a CVE will show other Actors in our database that have exploited the same CVE, and have the option to Compare them. Additionally, you can use the three dot drop-down menu to: Search in Vision to begin researching a CVE within the DarkOwl Vision dataset. See in Mitre to open a new browser tab and read more about the CVE from Mitre’s cve.org website. |