Leak Context
If a search result is from a data leak, an additional Leak Context View Switch will appear below the Metadata View Switch. Leak Context is information from the DarkOwl analyst team that gives additional enrichment regarding the leak, and may include relevant dates, content information, and target information.
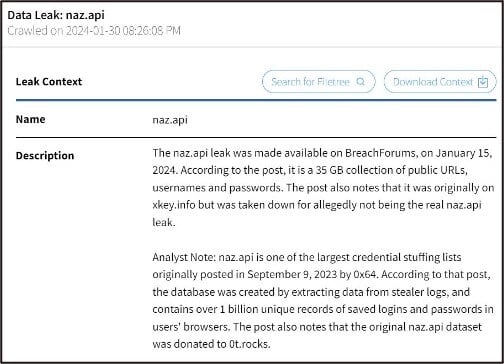
Some of the actions you can take include:
- Click Search for Filetree to locate and review the leak’s filetree document(s) (if filetree is available). The filetree will provide a list of all of the files that were available in the leak, including files that were not indexed by DarkOwl Vision. This can help you review for non-text content that might be relevant to your investigation.
- Click Download Context to download the leak context (.txt) to include in reports or briefings. This option is available in active client accounts.
- Click on the Vision Document ID link to open the Vision document to see the original post in a new search tab. This can help investigate the source of the leak further.
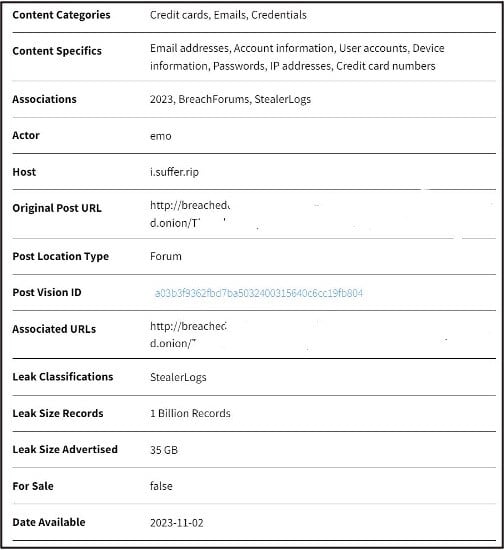
The following table provides a description of fields that may appear in Leak Context. Note: not all fields may be available or known for all leaks. Additional fields may be added in the future.
|
Name |
Name of the leak. |
|
Description |
A short description about the nature of the leak. |
|
Date Available |
Date the data was made available on the darknet or internet, if known. |
|
Date Breached |
Date of the leak incident or ransomware attack, if known. |
|
Content Categories |
High-level categories or types of content contained in this data leak. Content Category examples include: combolist, credentials, documents, messages, PII, stealerlogs, etc. |
|
Content Specifics |
More granular information about the compromised data in this leak. Content Specifics examples include: dates of birth, email addresses, financial documents, internal documents, ip addresses, legal documents, plaintext passwords, phone numbers, physical addresses, profile information, usernames, etc. |
|
Password Format |
Format of passwords found in the leak, if applicable, such as: plaintext, hashed, none, both. |
|
Password Hash Formats |
If the leak contains hashed passwords, this field will display what hashing algorithm is used, if known. Examples: MD5, SHA1, etc. |
|
Associations |
Any entity (site, organization, country, year, etc) that is associated with the data leak. Values in this field are searchable with the leak: operator. |
|
Actors |
Username(s) of the original poster or actor responsible or otherwise involved in leaking the data. Values in this field are searchable with the leak: operator. |
|
Attack Types |
The type of attack that resulted in the data leak. |
|
Targets |
The target organization or company where the data originated, if known. This is generally the name of the organization(s) attacked. If known, this field will optionally return Target Name, Target Domain, Target Description, and/or Target Country. |
|
Countries |
Country associated with the leak; for leaks related to a country without an organization Target. |
|
Hosts |
Site name(s) on which the original data was hosted. Values in this field are searchable with the leak: operator. |
|
Download Locations |
The URL where the leak was downloaded. |
|
Original Post URL |
The URL of the post in which the leak was initially shared. |
|
Original Telegram Channel |
The Telegram Channel ID in which the leak was initial shared. |
|
Post Location Type |
A classification of the location on which the leak was initially shared. Examples include: forum, leak site, marketplace, messaging platform, telegram, torrent, etc. |
|
Post Vision ID |
The document ID of the original post in the DarkOwl Vision index, if known. |
|
Associated URLs |
Any additional URLs that may be associated with this leak. |
|
Leak Classifications |
A classification of the nature of the leak. Examples include: Combolist, Cyberwar, Politically Motivated, Ransomware, Stealerlogs, etc. |
|
Leak Size Records |
The total number of records contained in the leak. |
|
Leak Size Actual |
The actual size of the leak, once downloaded. |
|
Leak Size Advertised |
The advertised size of the leak, from the original post. |
|
Completeness |
In some cases, partial or sample data is leaked by an actor. This field will display Partial if it is known that the leak dataset is not complete. |
|
For Sale? |
In some cases, leak data is offered for sale prior to being released on the darknet by an actor. If known, this field indicates whether the leak content was ever offered for sale. Note: DarkOwl adheres to a strict collections policy guided by CCIPS best practices and we do not purchase leak data or facilitate criminal activity. |
|
Filetree |
The name of the filetree document in DarkOwl Vision. Values in this field are searchable with the leak: operator. |
|
Public Reporting |
Any URLs, dates, or notes related to public reporting about this leak. |
|
Media Reporting |
Any URLs, dates, or notes related to media reporting about this leak. |